Can Your Crypto Wallet Be Hacked? 7 Common Threats & How to Protect Your Digital Assets

As virtual currencies like Bitcoin and Ethereum become mainstream, a critical question arises for every investor: can the money in my wallet be stolen? The short answer is yes, but understanding how and why is key to securing your assets. Unlike traditional bank accounts with fraud protection, cryptocurrency transactions are irreversible. This guide provides a comprehensive overview of the security landscape for crypto wallets, detailing common threats, from phishing scams to sophisticated hacks, and offering actionable strategies to fortify your digital wealth against theft.
Understanding Crypto Wallets: Hot vs. Cold Storage
Before diving into security threats, it's crucial to understand wallet types. A "hot wallet" is connected to the internet, such as software wallets on your phone or computer and accounts on exchanges. They offer convenience for frequent trading but are inherently more vulnerable. A "cold wallet," like a hardware wallet (e.g., Ledger, Trezor) or a paper wallet, stores your private keys offline. This "air-gapped" nature makes them highly resistant to online hacking attempts, making them the gold standard for storing significant amounts of cryptocurrency long-term.
Common Ways Crypto Wallets Get Hacked and Funds Stolen
Crypto theft doesn't always involve complex code-breaking. More often, it exploits human error or system vulnerabilities. Key threats include:
Phishing Attacks: Scammers create fake websites, emails, or social media messages mimicking legitimate services (like wallet providers or exchanges) to trick you into entering your seed phrase or private keys.
Malware and Keyloggers: Malicious software can infect your device to record keystrokes, capture screen data, or even replace a wallet address in your clipboard with the thief's address during a transaction.
Centralized Exchange Hacks: When you keep funds on an exchange like Coinbase or Binance, you trust their security. Major exchange breaches have led to losses totaling billions. Remember: "Not your keys, not your crypto."
Sim Swap Attacks: Hackers socially engineer your mobile carrier to port your phone number to a SIM card they control, allowing them to intercept SMS-based two-factor authentication (2FA) codes.
Weak Security Practices: Using simple passwords, reusing passwords across sites, storing seed phrases digitally (e.g., in a cloud note, text file, or email), or sharing sensitive information.
Smart Contract Exploits: For DeFi (Decentralized Finance) users, interacting with a malicious or poorly audited smart contract can grant it permission to drain your connected wallet.
Physical Theft and Coercion: If someone gains physical access to your hardware wallet and PIN, or forces you to unlock it, your funds can be stolen.
How to Protect Your Crypto Wallet from Theft: Essential Security Steps
Proactive security dramatically reduces your risk. Implement these best practices:
Use a Hardware Wallet for Major Holdings: For any substantial savings, transfer funds to a reputable hardware wallet. It keeps your private keys isolated from internet-connected devices.
Guard Your Seed Phrase with Your Life: Your 12 or 24-word recovery phrase is the master key. Never digitize it. Write it on a durable material (like metal) and store it in multiple secure, offline locations—never in a bank safety deposit box alone.
Enable Strong, Non-SMS 2FA: Always use Two-Factor Authentication, but avoid SMS. Opt for an authenticator app like Google Authenticator or Authy, or a security key like YubiKey.
Practice Digital Hygiene: Use a dedicated, clean computer or phone for crypto activities if possible. Install reputable antivirus/anti-malware software, keep all systems updated, and be wary of downloading unknown files or clicking suspicious links.
Verify Everything, Trust Nothing: Double-check wallet addresses before sending funds (check the first and last few characters). Always navigate to exchange or wallet websites directly, not via links in emails or messages.
Limit Exchange Exposure: Only keep the amount of crypto you need for active trading on an exchange. Treat exchanges like a checking account, not a savings account.
Use a Separate Email for Crypto: Create a new email address used exclusively for your cryptocurrency accounts to minimize exposure in data breaches.
What to Do If Your Crypto is Stolen?
While recovery is difficult, immediate action is critical. First, move any remaining funds to a new, secure wallet immediately. Report the theft to the relevant authorities (like the FBI's IC3 in the US) and the platform involved (exchange, wallet provider). While blockchain transactions are public and traceable, recovering stolen funds often requires legal intervention and cooperation from exchanges where the thief may try to cash out. This underscores the importance of prevention.
Conclusion: Vigilance is Your Best Defense
The question "can the money in the wallet be stolen?" highlights the core responsibility that comes with cryptocurrency ownership. The decentralized nature of crypto puts you in full control, but also makes you the sole security manager. By understanding the threats—from phishing and malware to exchange risks—and adopting a layered security approach centered around cold storage, seed phrase protection, and relentless verification, you can significantly harden your digital assets against theft. In the world of crypto, security is not a one-time setup but an ongoing practice of vigilance and education.
“Can Your Crypto Wallet Be Hacked? 7 Common Threats & How to Protect Your Digital Assets” 的相关文章
比特币徘徊历史高点;一场数字世界的“拔河赛”
比特币徘徊历史高点:一场数字世界的“拔河赛”在数字货币的浩瀚海洋中,比特币,这位被誉为“加密之王”的先行者,正再次以其令人瞩目的姿态,逼近历史的巅峰。它如同一个技艺高超的舞者,在109,404美元的价位上灵活舞动,距离11万美元的里程碑仅一步之遥。然而,在市场的乐观情绪之下,一场看不见的“拔河赛”正...
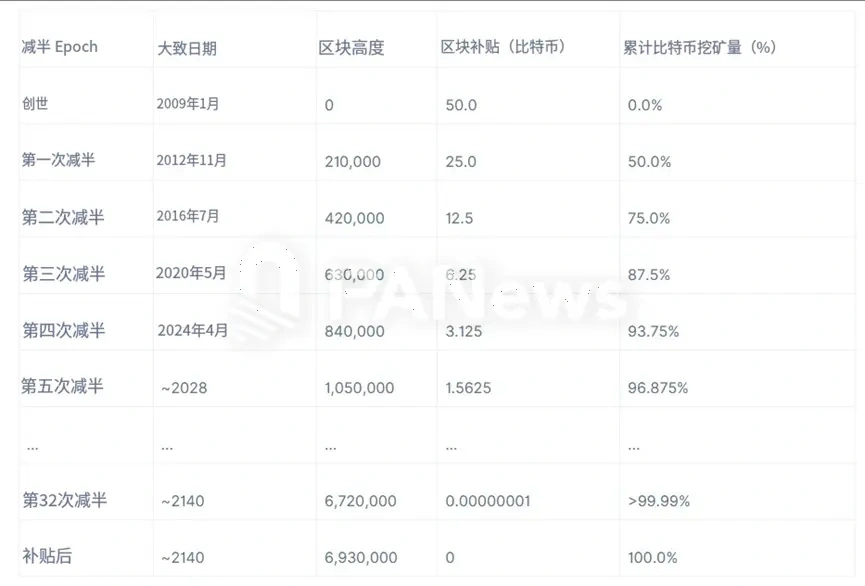
当2100万比特币全部被挖出后会发生什么?
大约在 2140 年左右的某个时间,市场上将不再有新的比特币发行。所有 2100 万枚比特币都将被分发完毕,这意味着比特币矿工将只能以交易费的形式获得奖励。批评人士认为,仅靠交易手续费不足以维持比特币网络的安全。关键要点2140 年之后,区块补贴将不复存在。比特币矿工对于处理交易和保障网络安全至关重...
比特币资金费率详解 | 永续合约价格锚定的核心机制
比特币资金费率:永续合约市场的关键机制更新时间:2025年7月27日 | 作者:加密货币衍生品分析师什么是比特币资金费率?比特币资金费率是永续合约市场中特有的机制,用于确保合约价格与标的资产现货价格保持长期一致。与传统期货合约不同,永续合约没有到期日,资金费率机制替代了传统的到期结算方式。资金费率的...
巨鲸的告别;比特币灵魂深处的哲学辩论
巨鲸的告别:比特币灵魂深处的哲学辩论目录:· 序章:一笔惊世交易的涟漪· 巨鲸浮现:8万枚比特币的易主· “信仰动摇”论:斯科特·梅尔克的火花· 观点的交锋:何谓“背叛”?· 传统与新生:两种未来的拉扯· 中本聪的初衷:去中心化的乌托邦·&...
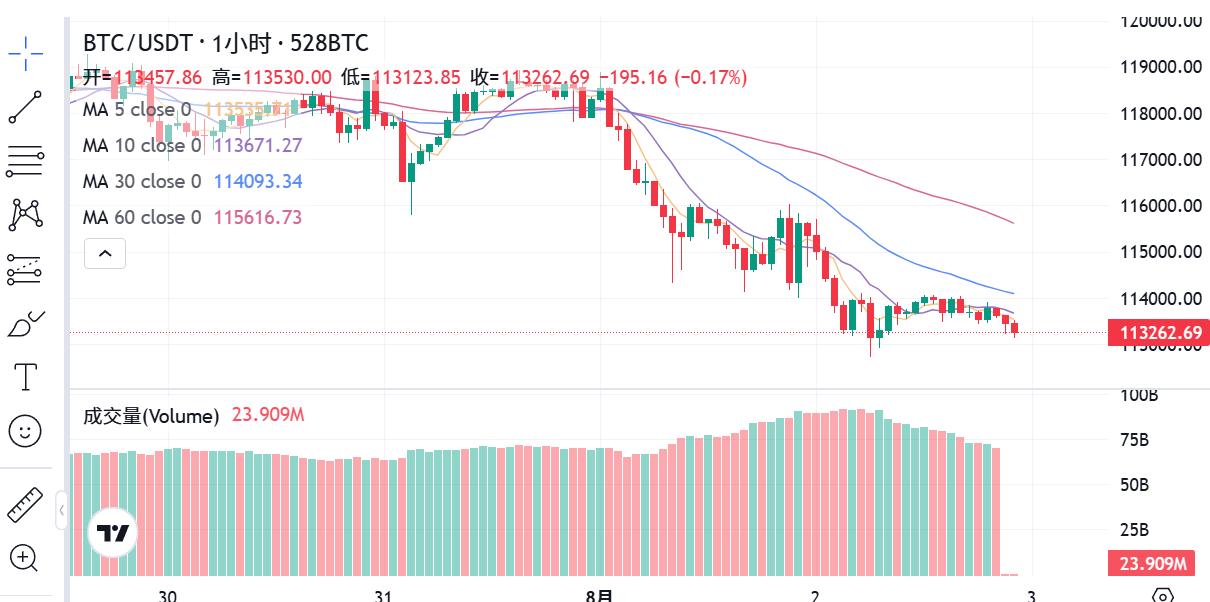
BTC最新成交量分析:市场流动性深度解读
BTC最新成交量分析:市场流动性深度解读最后更新:2025年8月2日目录成交量概览成交量趋势分析交易所成交量对比大额交易追踪市场流动性评估成交量与价格关系成交量技术指标投资洞察常见问题BTC成交量概览截至2025年8月2日,比特币24小时全球交易量达到580亿美元,较上周平均水平增长35%。其中现货...
监管之手与期权魔术;高限额期权如何重塑比特币波动,并引爆现货需求
监管之手与期权魔术:高限额期权如何重塑比特币波动,并引爆现货需求?标签: 比特币ETF 期权交易 SEC 波动率 现货需求 机构投资目录:· 序章:告别狂野,走向成熟· SEC的新规:期权限额的“十倍”放大· 期权策略:用“卖权”平滑波动· 波动率的下降:比特...